The illustration of G-code file format.
$ 31.99 · 5 (379) · In stock

Download scientific diagram | The illustration of G-code file format. from publication: Self-embedding watermarking method for G-code used in 3D printing | 3D printing is faced with a lot of security issues, such as malicious tampering, intellectual property theft and so on. This work aims to protect the G-code file which controls the 3D printing process by proposing a self-embedding watermarking method for G-code file. This | Watermarking, 3D Printing and clinical coding | ResearchGate, the professional network for scientists.

Metadata added to G-Code — WAZER Support
The shapes of the 3D prints corresponding to the four G-code files used
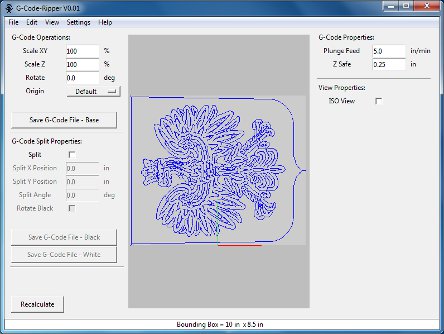
G-Code Ripper

Z Axis Probing Issues - General Discussion - Klipper, g1 f1200 gcode
Collision rate versus number of trial runs for hashing an input stream
![]()
G Code File 3D Illustration Icon 33211376 PNG

G-code Explained List of Most Important G-code Commands
gcode · GitHub Topics · GitHub
Maximum per-layer attack concentration, averaged across multiple runs
![]()
Premium PSD G code file 3d illustration icon

Z Axis Probing Issues - General Discussion - Klipper, g1 f1200 gcode

The authentication code embedding procedure

Ayanokoji Kiyotaka Stickers for Sale, ayanokoji kiyotaka

HASHTAG detection rate versus the number of checkpoint layers used for