A) Schematic showing key parameters of breach width (Bw) and breach
$ 16.50 · 4.9 (272) · In stock

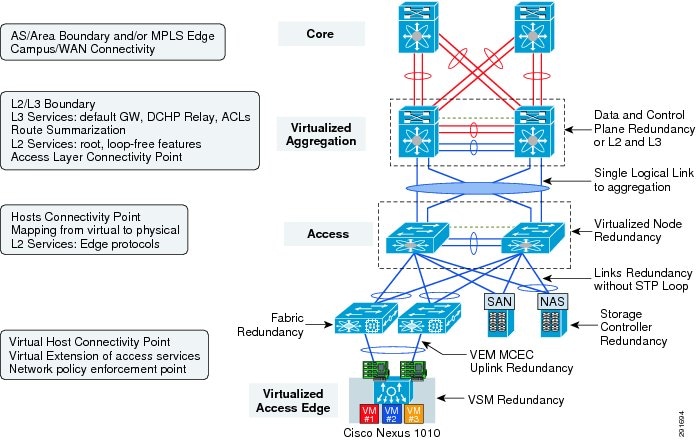
Cisco Virtualized Multi-Tenant Data Center, Version 2.1, Design

Owen KING, PhD Student

Analysis of Uncertainty and Sensitivity in Tailings Dam Breach

How natural foreshores offer flood protection during dike breaches
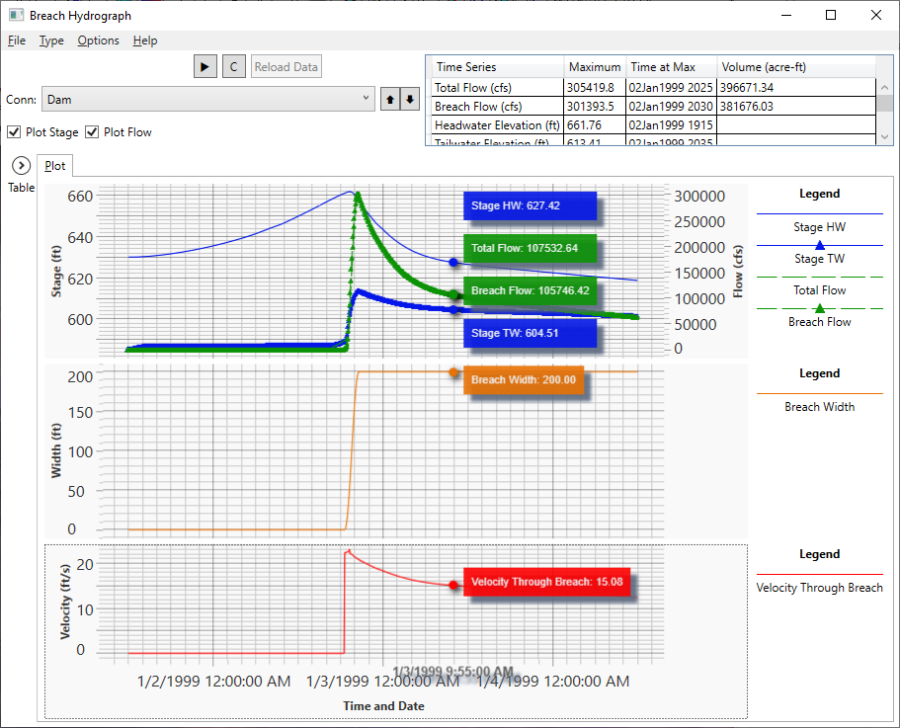
Breach Hydrograph Plot

Simulation of Dam-Breach Outflow Hydrographs Using Water Level

Ashim SATTAR Assistant Professor IIT Bhubaneswar; Former Faculty

Breaching Active Directory tryhackme, by abdellah oullaij

Atanu BHATTACHARYA, PostDoc Position
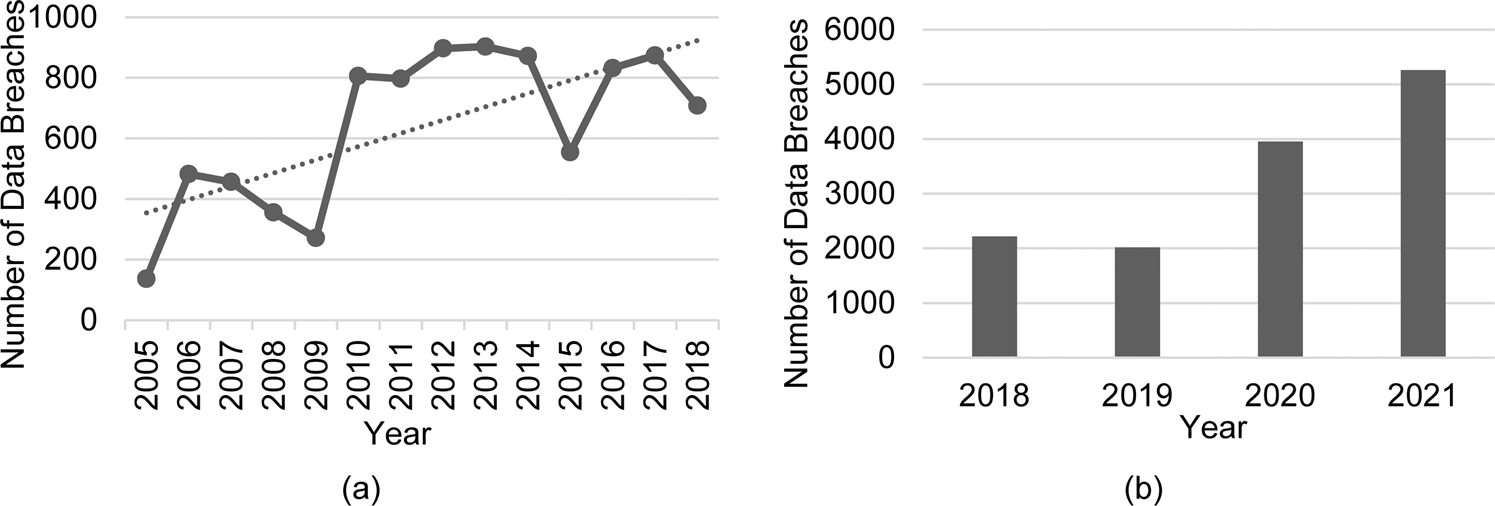
Data security crisis in universities: identification of key